Together with another resident, I have review the public records pertaining the wire fraud that happened in August and that unfortunately led to a loss of ~ $50k of the taxpayer’s money. Below are some details and a conclusion.
Fraud approach
The fraudster was sending emails that used the exact same email address as the Mayor. He or she sent it to the Town’s email system from outside. This is commonly known as email spoofing and is relatively simple to do. Normally, any reply to a spoofed email would go back to the Mayor’s proper address. However, in this case the sender also added another email trick. The fraudster added a separate reply-to address into the email. A separate reply-to address that is different from the senders is a standard feature in email but is not commonly used. The reply to address that showed up once you hit reply was an outlook.com address. This is a free consumer grade email address that anybody can sign up to.
The Fraudster asked the Town to wire money to a different bank. From there, the money probably went through multiple additional wire transfers until they finally reached the fraudster.
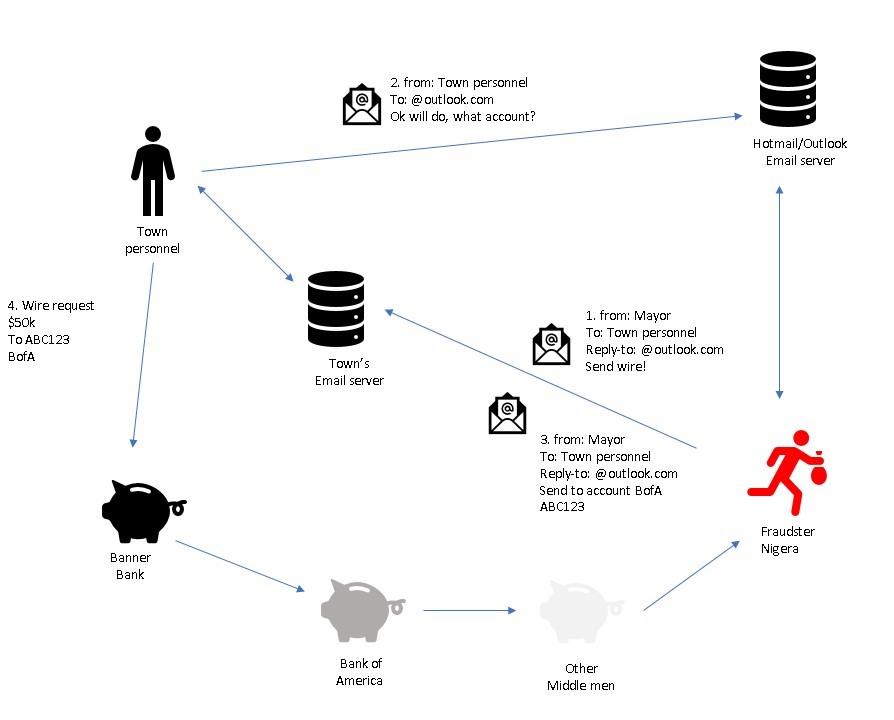
- Fraudster sends “phising” email impersonating the Mayor and asking for a wire transfer.
- Town personnel replies and ask what account to transfer money to.
- Fraudster copy/paste email from outlook server and replies again with an email impersonating the Mayor.
- Wire is sent out. Fraudster typically is using several layers of wire transfers to receive the money.
Timeline
July 12th – Failed attempt to fraud. This attempt was flagged by the Clerk/Treasurer and sent to the IT- administrator. Clerk/Treasurer notes that she is getting a suspicious reply-to email address when she hits reply.
Aug 16th – Successful attempt that resulted in ~ $14k being wired out of the Town’s account.
Aug 21st – Successful attempt that resulted in ~ $35k being wired out of the Town’s account.
Aug 22nd – Mayor discovers the fraud. Police and FBI informed.
Sept 1st – Yet another request for wire transfer received. This was flagged as fraud.
Conclusion
- This was a classic and common type of phishing email.
- Town’s email system lacked good spam/fraud protection. An email coming from Nigeria with this type of odd header should have been flagged and deleted by the system. As of 10/17/2017 The Town’s website is indicating that they are upgrading their email system.
- Town’s email system does not use Sender Policy Framework and is therefore susceptible to spoofing. This is still the case as of 10/17/2017.
- The sender’s IP-addresses from can be traced back to Smile Telecom in Nigeria. This means that a system in Nigeria sent the fraudulent email that initiated the wire transfer.
- Sender knew names and short names of people working in the Town’s administration. This information was potentially harvested from the Town’s website. However, some of the names used were not mentioned on the town’s website at the time of the fraud. The harvesting must have taken place earlier in the year.
The chances that the perpetrator will be found is probably slim at this point. But not all hope is lost. There are avenues open that I know the Mayor is exploring to try to recoup some or all the money. I’m happy to assist in any way I can. If I get elected to the Town council on November 7th, I believe that my background in IT, Networking and Security will be helpful to make sure the town have a modern IT infrastructure.

In my opinion the human failures on this wire fraud were far more troubling than email security. The town has not sent any wires in the past 10 years, perhaps never. Why did the bank send these wires without checking with the town and getting an explanation? The Mayor isn’t authorized to unilaterally spend money without council approval. Why were these wires processed at all without that approval? The emails contain obvious grammatical and punctuation errors. The recipients names were not ones that it made much sense to receive money from the town, and one of the recipients was completely changed at the last minute. The whole thing stinks to high heaven and any normal common sense should have questioned this. The real question is why substantial sums of money could be wired out at all without there being checks and balances that would have blocked it. Judgment errors and inadequate controls, in my opinion. And why doesn’t the audit test for such controls?
I’m with you on the comment made by Carl. This sounds so phony it makes my head spin. Why would anyone send anything without a checks and balances approach? This sounds fishy….I hope the real reason this happened is uncovered…I don’t think we’re getting the whole story here. What a weird thing to happen…and so preventable.
Very strange.
I did a public records request. The records support Carl’s conclusion that “The whole thing stinks to high heaven and any normal common sense should have questioned this.”
The Town’s employees and contractors allowed two wire transfers of $49,248 of Town funds to go to fictitious accounts without documentation or authorization.
On June 13, the Fiscal Coordinator (a contractor) and the Clerk Treasurer (an employee) received odd emails supposedly from the Mayor asking if they were “at the office.” On July 3 the Fiscal Coordinator received another email from the “Mayor” asking if he was at his desk. The return address was “headj963@gmail,” not the Mayor’s address.
On July 12, the Clerk Treasurer received another email supposedly from the “Mayor” asking her to take care of a wire “real quick.”
She forwarded the email to the Mayor, asking, “Did you send this?” She also alerted the Town’s IT Administrator, a contractor: “Seems suspicious, is this something to worry about? When I hit reply the reply-to address was Mayor [email protected]. The next day the IT Administrator responded: “Not sure, looks phishy though… we’ll have to see if Dicker [the Mayor] sent it…” At this point, it appears that the Clerk Treasurer, the IT Administer, and possibly the Mayor ALL knew something suspicious was going on but no one seems to have taken any further action to stop the fraud.
In fact, no one seemed to have raised an eyebrow when the “Mayor” again on August 16 asked the Fiscal Coordinator at 7:24 am and the Clerk Treasurer at 7:23 if they were “at the office.” This is curious because the real Mayor certainly knew the Town office doesn’t open until 8:30 am.
At 8:29 the Fiscal Coordinator emailed the Mayor at “[email protected]” (not the real mayor’s address), “No I am working from home.” Three minutes later, the supposed “Mayor” asked: “Can you process an outgoing wire transfer for me today? Let me know if you can handle that from home so I can send you the wire details.”
At 9:05, the “Mayor” told the Fiscal Coordinator to send a wire transfer to an account at Compass Bank in Birmingham, Alabama, for $14,624. “I will send you the invoice and all supporting documents later.”
At 9:14, the “Mayor” sent a second, identical email to the Fiscal Coordinator with a copy to the Deputy Clerk. At 10:36, the Deputy Clerk sent the user name and password for the Town’s Banner Bank account to the Fiscal Coordinator. Three minutes later, the “Mayor” emailed that a change was needed and he requested the funds be sent to a Bank of America account in New York.
On the same day, Banner Bank transferred the funds, but sent SIX security alerts to the Fiscal Coordinator. Now both the Deputy Clerk and the Fiscal Coordinator knew about this highly irregular transfer of funds.
A week later on August 21, the “Mayor” emailed a request to the Fiscal Coordinator to “handle a wire transfer for me today.” He then directed transfer of $34,624 of the Town’s funds to an account at Suntrust Bank in Tampa, Florida. Banner Bank created the wire transfer and AGAIN sent a security alert to the Town.
The next day, August 22, the “Mayor” requested a wire transfer of $64,624 to the bank in Florida. FINALLY, on September 1, Town employees realized something was wrong and advised Banner Bank that this was a “continuing fraud.”
Why did it take the Town employees almost THREE MONTHS to come to this conclusion? Lack of common sense and negligence, or worse, have cost the Town over $49,000. We MUST hold those who are responsible, accountable for this loss.
This seems so preventable. Who is accountable for this?